Context is King: Elevating Your Security Posture Beyond the Password
In today's hyper-connected and increasingly sophisticated threat landscape, relying solely on traditional authentication methods like passwords is akin to locking a high-security vault with a simple house key.
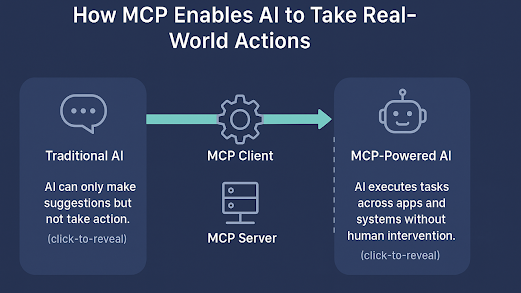
In my last article we looked at PassKey and it's importance in 2025. Context-Aware policy enforcement will make sure even more tougher authentication.
The business world demands a more robust, adaptive, and intelligent approach to safeguarding its valuable assets and sensitive data. The answer? Context-Aware Policy Enforcement.